Secure Deletion in Flash Memory
Research into secure deletion on flash storage devices.
What is Secure Deletion?
The definition of what constitutes a "secure" deletion will be dependent on the specific use case. One possible definition is a deletion from which the deleted data cannot be recovered, which is probably the most common definition. Another more strict definition would a deletion where no information about the deleted data can be recovered. This stricter definition focuses on the concept of a structural or informational artifact. These artifacts might be a pattern that is broken or changed due to the deletion. For example, if you have a series of log files from a cron job that runs hourly, and you delete a single file from the logs, even if you delete the file in a manner that makes it unrecoverable the fact that it existed is still silently embedded in the presences of the neighboring files.
My Research
My research was focused on secure deletion in hardware that utilized NAND flash storage. The reason for this focus is that flash memory fundamentally tends to create structural artifacts below the operating system layer. With traditional block storage devices, the operating system secure deletion involves assumptions about the underlying hardware. With flash storage there is a layer of firmware on the storage device, which emulates the behavior of a block device (for the purpose of interoperability), but how it actually stores the data is dependent on the specifics of the firmware. Flash firmware typically uses a log structured writing scheme, which means that when information is written to a device it is written in sequential order (like the cron job example). This method of writing means that deletion creates gaps that show up at the flash layer where missing data used to be. This is a structural artifact, which could be used to leak information about the data being stored.
My research was into the usage of Full Disk Encryption (FDE) technologies like Bitlocker or Truecrypt as a method of removing or hiding these structural artifacts in flash memory. If FDE proved to be an effective solution, then instead of having to address the issue by having custom firmware with the purpose of supporting secure deletion, you could address the problem at the block device layer with a FDE scheme on regular consumer grade flash devices.
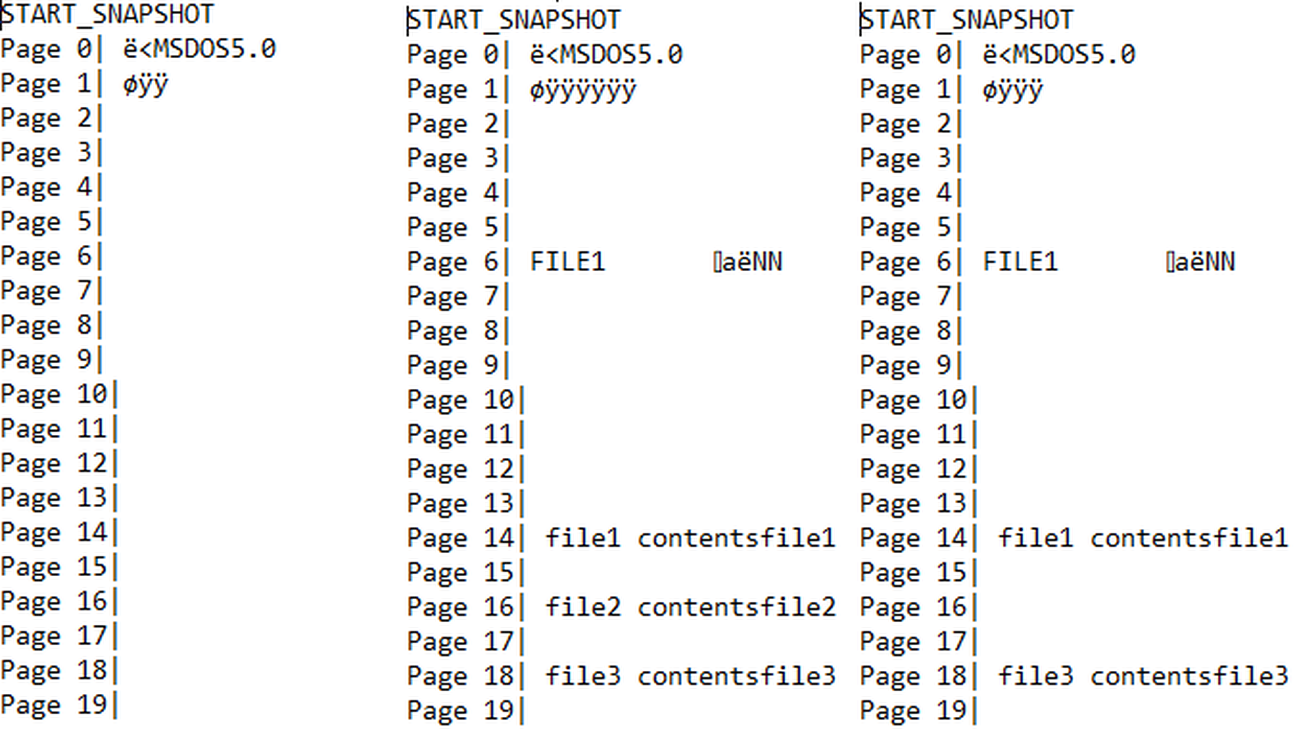
I created a modified version of the OpenNFM flash firmware on a development board, which allowed me to emulate a flash device, but with custom firmware. With my firmware, I devised a method of taking a snapshot of all the raw data on the device. I then performed experiments by adding files to the flash drive in plain text, and testing multiple FDE schemes to see if structural artifacts could be observed from deletions. The results I found were that artifacts could be observed still, but that because the artifacts were still encrypted it may be difficult to determine information about them.